MERKLE TREES
A Merkle tree is a data structure used in Bitcoin blockchain technology. The tree is constructed by recursively hashing pairs of leafs until reaching the top. The final hash is called the Merkle Root, and is a representation of all transactions included in a Bitcoin block.
This project will include source code for obtaining data from www.blockchain.info using GET requests in python and recreating the Merkle Root by recursively hashing the transactions in a block.
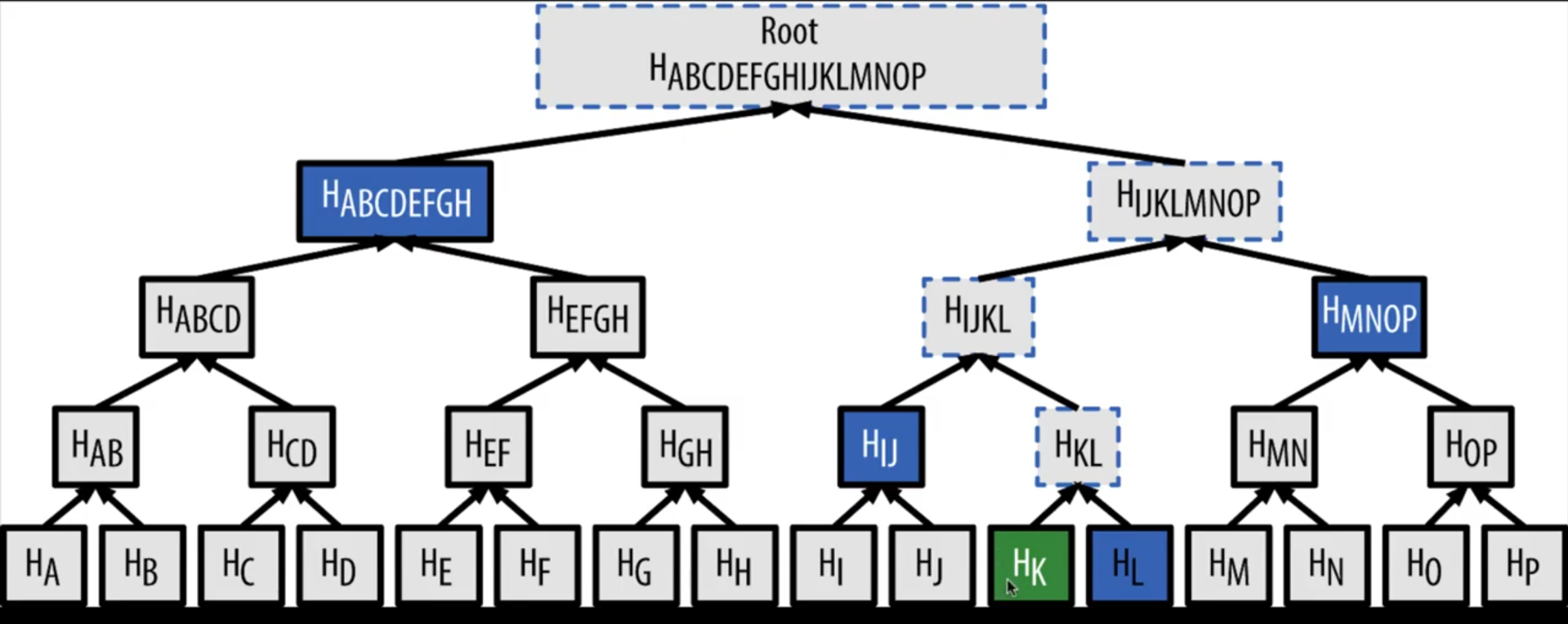
Picture of a Merkle Tree obtained from Edd Man's Youtube Channel
HASHING
Encryption is the process of encoding a message or information that only authorized parties can access, not allowing unauthorized personal to access. Bitcoin utilizes an encpryption based on the EllipticCurve Digital Signature Algorithm(ECDSA), along with the elliptic curve secp256k1.
Bitcoin also utilizes The Secure Hash Algorithm(SHA) to hash transactions securely. There are a few variation of SHA consisting of SHA256 and SHA1 used in bitcoin.
This project will analyze and compare different encryption methods that are used in bitcoins with other encpryption methods outside of bitcoin.
 Picture of Sha256 Hashing obtained from
BlockGeeks.com
Picture of Sha256 Hashing obtained from
BlockGeeks.com
CONSENSUS
A consensus algorithm may be defined as the mechanism through which a blockchain network reaches consensus. Public blockchains are built as distributed systems for which they do not rely on a central authority, the distributed nodes need to agree on the validity of transactions.
This is where consensus algorithms come into play. They assure that the protocol rules are being followed and guarantee that all transactions occur in a trustless way, so the coins are only able to be spent once.
Consensus algorithms are crucial for maintaining the integrity and security of a cryptocurrency network. They provide a means of distributed nodes reaching consensus on which version of the blockchain is the real one. Agreeing upon the current blockchain state is essential for a digital economic system to work properly
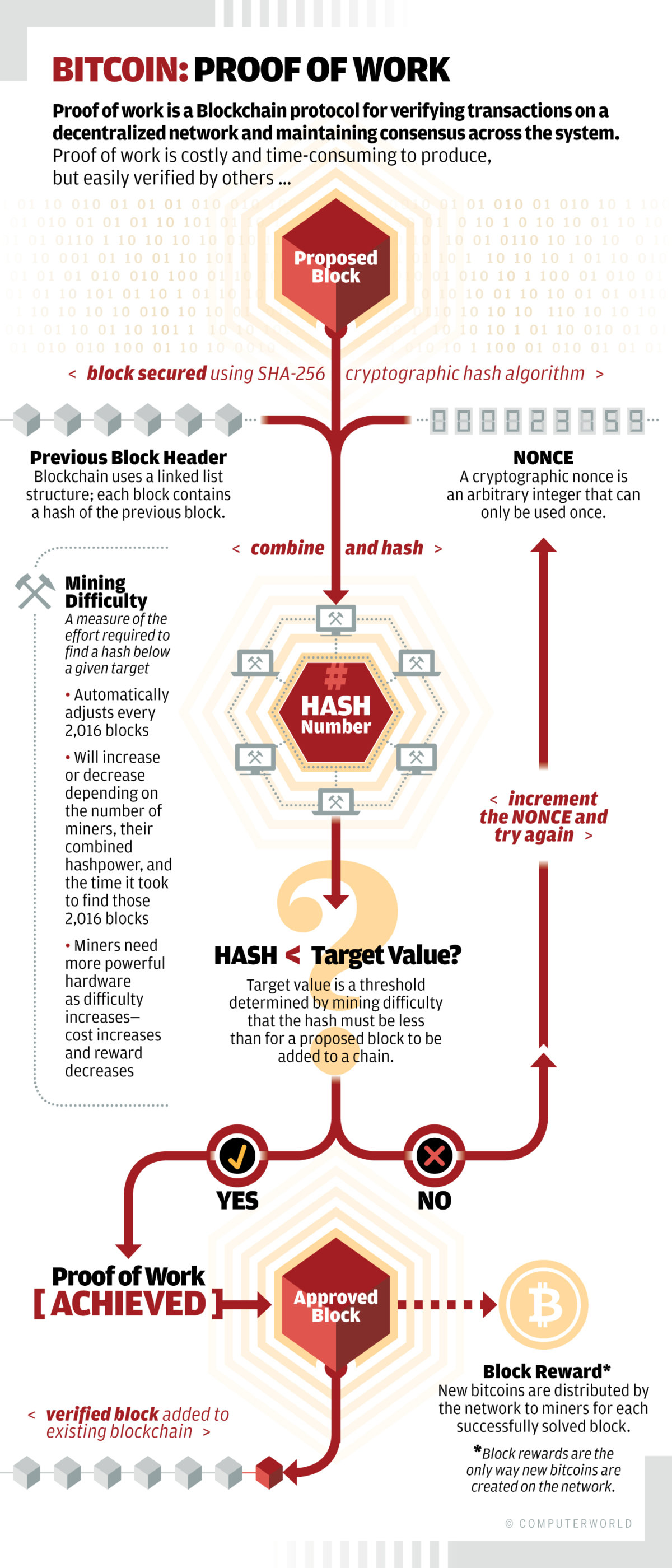
Picture of Consensus obtained from ComputerWorld.com
Go to Top