Resources
Learn Me A Bitcoin
Sergio's Blockchain Playlist
Blockchain.info
Bitcoin.org
Investopedia: Blockchain
Blockonomi: Merkle Trees
JRE: Ben Goertzel
MERKLE TREES
Introduction
(For a better experience, we recommend looking at this page in a laptop or desktop)Let's begin with a simple concept: One-way hashing functions.
A one-way hashing function is a simple mechanism that takes in something as an input and produces a unique hash value for it. The hashing function we will be using is called SHA-256.
Let's try it. Input some text into the box below and click the "Hash It!" button.
Whatever text you hashed, should always produce the same result. For instance, you can go to this website and enter the same text you entered in the "Hash It" box and you should get the same output.
This presents a very interesting possibility. Could I also do this with a file? The answer is "Yes". You can put a file through a hashing function and get a hash value. Then, other people can verify the contents of the file by downloading the file and using the same hashing function to produce a hash value. Let's see an example.
Imagine you have a simple zip archive with 4 files in it. The achive is on the web somewhere. You need to download it and make sure that the file downloaded correctly. In other words, you have to verify that the archive you have is the same as the one that was uploaded to the web site.
The archive contains the following files:
- blockFunctions.js
- consensus.html
- index.html
- merkle.html
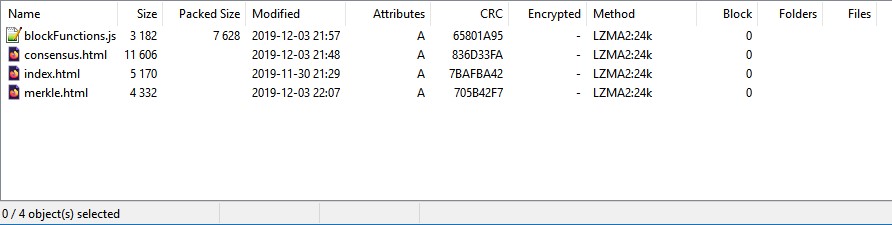
By using a hashing utility such as CRC SHA, which usually comes installed with 7-zip, we can hash the contents of the whole zip archive and get a result.
By clicking on the * simbol, we can get all the resulting hashes.
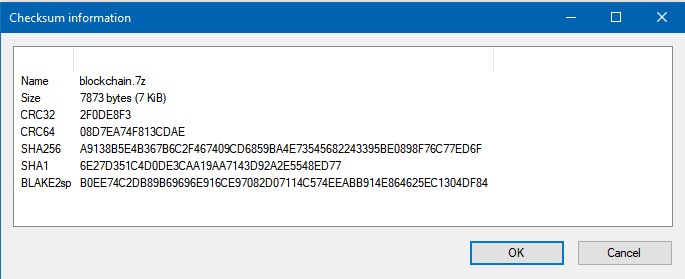
If you go to the repo page, you can download this zip file and hash it. You should get the same results as shown on the image above.
Merkle Trees Explained
Now that you are familiar with hashing, let's look at how it fits in with merkle trees.
A merkle tree is a data structure that is made out of hashes. Merkle trees are based on binary search trees. But each node in the tree is a hash of it's two child nodes.
Typically, the leaf nodes at the bottom of the tree, are the hash of something real. That means the leaf nodes of the tree usually represent actual files. In our prior example, we could hash each file individually and then use the merkle tree algorithm to build the tree.
Once the merkle tree is built, the top hash is called the merkle root. The merkle root is a representation of a whole unit.
In Bitcoin's merkle tree algorithm, each leaf node is the hash of a transaction. A transaction is a record of an exchange of bitcoins between different parties. Each transaction is hashed using the SHA-256 algorithm. This process is similar to how we can use the CRC SHA utility to hash a zip archive.
But Bitcoin's algorithm uses a SHA-256 double hash. Fancy term, it just means that you hash something and then you hash the hash. Confused? Let's try it. Remember our hash it box? We'll use it again. Enter something in the text box and then hash it.
Delete your original text from the box. Then, copy the resulting hash value and paste in the box. Click Hash It! again.
Let's see a real example. Block 150000 in the Bitcoin blockchain has the following transactions hashes (also known as IDs):
- bcdc61cbecf6137eec5c8ad4047fcdc36710e77e404b17378a33ae605920afe1
- f7f4c281ee20ab8d1b00734b92b60582b922211a7e470accd147c6d70c9714a3
- b5f6e3b217fa7f6d58081b5d2a9a6607eebd889ed2c470191b2a45e0dcb98eb0
- 4206f171f06913b1d40597edcaf75780559231fb504c49ba85a4a9ae949e8b95
- a1a6ad6ff321c76496a89b6a4eb9bcfb76b9e068b677d5c7d427c51ca08c273d
- 89c82039452c14a9314b5834e5d2b9241b1fdccdb6e4f4f68e49015540faaf95
- 25c6a1f8c0b5be2bee1e8dd3478b4ec8f54bbc3742eaf90bfb5afd46cf217ad9
- 57eef4da5edacc1247e71d3a93ed2ccaae69c302612e414f98abf8db0b671eae
- 8d30eb0f3e65b8d8a9f26f6f73fc5aafa5c0372f9bb38aa38dd4c9dd1933e090
- 13e3167d46334600b59a5aa286dd02147ac33e64bfc2e188e1f0c0a442182584
These hashes are the result of hashing all the information in a transaction to come up with a unique fixed-length value that identifies the transaction with respect to the entire blockchain.
Bitcoin's algorithm takes pairs of hash values and hashes them together to come up with a new hash value. If the number of hash values is odd at any given level of the tree, the last hash is hashed with itself. This simple process is repeated until reaching the top of the tree. At that point, the last resulting hash is the Merkle Root.
Below is a break down of how the process takes place.
Round 1
In the first round, the given 10 transaction-hash values are paired up. The text in red represents the original transaction hash and the text in blue represents the resulting hash value of hashing a pair of transactions. 10 go in, 5 come out.
- bcdc61cbecf6137eec5c8ad4047fcdc36710e77e404b17378a33ae605920afe1
- f7f4c281ee20ab8d1b00734b92b60582b922211a7e470accd147c6d70c9714a3
- b717aaa5ceb29408c29ad9bb3e76b9e38e6193f7d5e8a513af7e67144e77a2a4
- b5f6e3b217fa7f6d58081b5d2a9a6607eebd889ed2c470191b2a45e0dcb98eb0
- 4206f171f06913b1d40597edcaf75780559231fb504c49ba85a4a9ae949e8b95
- 15b11efcaa44c295d0717ba1c3cf5671a597730a1db9c1b86f8059f0813c2140
- a1a6ad6ff321c76496a89b6a4eb9bcfb76b9e068b677d5c7d427c51ca08c273d
- 89c82039452c14a9314b5834e5d2b9241b1fdccdb6e4f4f68e49015540faaf95
- b93dd0cd83452310779b833aa78785e1c0232a738ffa9dc7004fff87dbb3c2ef
- 25c6a1f8c0b5be2bee1e8dd3478b4ec8f54bbc3742eaf90bfb5afd46cf217ad9
- 57eef4da5edacc1247e71d3a93ed2ccaae69c302612e414f98abf8db0b671eae
- 9697afe915067eaf057285c5a2a2acd85b782251773b7f0bc9c09e93d9d66a06
- 8d30eb0f3e65b8d8a9f26f6f73fc5aafa5c0372f9bb38aa38dd4c9dd1933e090
- 13e3167d46334600b59a5aa286dd02147ac33e64bfc2e188e1f0c0a442182584
- f8fa3616bcaf585a70834fe005e9278995be624f4da711229a1c0d009123c411
Round 2
In Round 2, the results from the previous round are paired up and hashed. Because the number of inputs is odd, the last hash is hashed with itself. Blue is the color of the input hashes, and violet is the color of the outputs. 5 go in, 3 come out.
- b717aaa5ceb29408c29ad9bb3e76b9e38e6193f7d5e8a513af7e67144e77a2a4
- 15b11efcaa44c295d0717ba1c3cf5671a597730a1db9c1b86f8059f0813c2140
- 49f1038d5b508972a08520a6510ba6673e2d005a97ee766d0e80abc28ffeb6f1
- b93dd0cd83452310779b833aa78785e1c0232a738ffa9dc7004fff87dbb3c2ef
- 9697afe915067eaf057285c5a2a2acd85b782251773b7f0bc9c09e93d9d66a06
- 47188a2399ab7a2f03b1ec13fb90565aed092b3bd46895073eef11abc25fe18b
- f8fa3616bcaf585a70834fe005e9278995be624f4da711229a1c0d009123c411(with itself)
- f8fa3616bcaf585a70834fe005e9278995be624f4da711229a1c0d009123c411(with itself)
- f72e6471cc51a3556a5cff6a11e49bf77c9cf8ea52e797adc6a54887b6448ce5
Round 3
In Round 3, the same process is repeated. The text in violet represents the results from the previous round. The text in black represents the resulting hashes. 3 in, 2 out.
- 49f1038d5b508972a08520a6510ba6673e2d005a97ee766d0e80abc28ffeb6f1
- 47188a2399ab7a2f03b1ec13fb90565aed092b3bd46895073eef11abc25fe18b
- ef1b0a05f99899ed905712577f2a7faa80ea8a72b3c401d7ee964e487b739d8d
- f72e6471cc51a3556a5cff6a11e49bf77c9cf8ea52e797adc6a54887b6448ce5(with itself)
- f72e6471cc51a3556a5cff6a11e49bf77c9cf8ea52e797adc6a54887b6448ce5(with itself)
- 74fae1ec2293482a1822a2bc6c5999c61713d24cd123bc9f68a2e71f1b3327e8
Round 4
In the final round, only 2 go in and the resulting hash is the Merkle Root.
- ef1b0a05f99899ed905712577f2a7faa80ea8a72b3c401d7ee964e487b739d8d
- 74fae1ec2293482a1822a2bc6c5999c61713d24cd123bc9f68a2e71f1b3327e8
- be0b136f2f3db38d4f55f1963f0acac506d637b3c27a4c42f3504836a4ec52b1(COMPUTED MERKLE ROOT)
Now, you hopefully have a better understanding of how a merkle tree is build on the Bitcoin blockchain. Check out the repo for the Python implementations and to look at the JavaScript source code. Also, if you didn't know, you can look at the source code for this page by using the developer tools in Chrome or Firefox. You can toggle developer tools by pressing Ctrl+Shift+I.
Go to Top